Edge computing is revolutionizing how we process and utilize data. It’s no longer just about moving data to the cloud; instead, it’s about bringing computing power closer to the source of data generation. This enables faster processing speeds, reduced latency, and enhanced security, making it ideal for a wide range of applications.
This in-depth exploration delves into the intricacies of edge computing, covering everything from its core principles and technologies to its deployment models, use cases, and future trends. We’ll also examine the benefits, challenges, and security considerations surrounding edge computing solutions.
Introduction to Edge Computing
Edge computing is a distributed computing paradigm that brings computation and data storage closer to the source of data generation. This proximity enables faster processing speeds, reduced latency, and enhanced security compared to traditional cloud-based architectures. It’s becoming increasingly crucial in a world demanding real-time data analysis and responsiveness.The core principle behind edge computing is decentralization. Instead of sending all data to a central cloud server for processing, edge devices perform the processing locally.
This approach optimizes performance and reduces reliance on high-bandwidth network connections.
Key Differences Between Cloud and Edge Computing
Cloud computing typically involves sending data to a remote data center for processing. Edge computing, on the other hand, processes data closer to its source, often on specialized hardware. This key difference translates into several critical advantages, including reduced latency, enhanced security, and better resilience to network disruptions.
Real-World Applications of Edge Computing
Edge computing finds applications in various sectors, each benefiting from the reduced latency and localized processing capabilities. Real-time video surveillance systems, for example, can process video feeds at the edge, enabling rapid detection of anomalies and minimizing delays in response.
- Industrial Automation: Edge computing is transforming manufacturing through real-time monitoring of equipment performance. This enables predictive maintenance, reducing downtime and improving overall efficiency.
- Autonomous Vehicles: Edge devices process sensor data in real-time, allowing for immediate responses and decision-making, a crucial aspect of autonomous driving.
- Smart Cities: Traffic management systems can use edge computing to analyze data from sensors in real-time, optimizing traffic flow and reducing congestion. Smart streetlights can also adjust brightness based on real-time data.
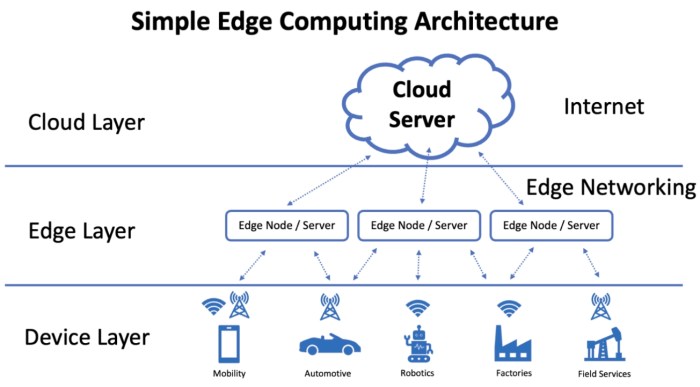
Basic Edge Computing System Diagram
This diagram illustrates a basic edge computing system.
| Component | Description |
|---|---|
| Sensors | Collect data from the environment, such as temperature, pressure, or motion. |
| Edge Device | Processes data from sensors, performing analysis and potentially making decisions. |
| Network | Connects the edge device to other devices or the cloud, facilitating data transfer. |
| Cloud | A central repository for data storage and additional processing, though less critical in edge-centric operations. |
A simple diagram would depict sensors connected to an edge device. The edge device then transmits processed data either to the cloud or directly to other devices. This depiction emphasizes the localized nature of processing.
Edge Computing Technologies
Edge computing relies on a diverse range of technologies to function effectively. These technologies facilitate the processing of data closer to the source, reducing latency and improving responsiveness. The interplay between these technologies is crucial for the successful deployment and operation of edge computing systems.
Enabling Technologies
Various technologies are fundamental to edge computing. These include powerful microprocessors, specialized hardware accelerators, and robust communication networks. The combination of these elements allows for efficient data processing and transmission, a key aspect of edge computing’s operational efficiency.
Sensors and Actuators
Sensors and actuators are integral components of edge computing systems. Sensors gather data from the physical environment, such as temperature, pressure, or location. Actuators, in turn, respond to the processed data by adjusting physical processes, for instance, controlling a valve or adjusting a machine’s settings. This closed-loop system allows for real-time responses and automation. For example, in a smart factory, sensors monitor equipment performance, and actuators adjust parameters in response, optimizing production and reducing downtime.
Communication Protocols
Edge computing systems utilize a variety of communication protocols to facilitate data transfer. These protocols, such as MQTT, AMQP, and CoAP, cater to different needs and characteristics of edge devices. MQTT, for instance, is well-suited for low-bandwidth, resource-constrained devices, while AMQP is suitable for more complex communication requirements. Efficient communication is crucial for the seamless flow of data within the edge network.
Edge Computing Platforms
Different edge computing platforms cater to varying needs and functionalities. Some platforms specialize in handling real-time data streams, while others focus on batch processing or data analysis. Cloud-based platforms, such as AWS Greengrass and Azure IoT Edge, provide a robust framework for managing and deploying edge applications. These platforms often offer features for device management, security, and data analytics.
A choice of platform is dictated by the specific requirements of the application.
Comparison of Edge Computing Technologies
| Technology | Pros | Cons |
|---|---|---|
| MQTT | Low bandwidth, resource-efficient, ideal for IoT devices | Limited complexity support, not suitable for high-volume data |
| AMQP | Robust messaging, high reliability, supports complex messaging patterns | Higher overhead compared to MQTT, requires more resources |
| CoAP | Lightweight, efficient for constrained environments, good for resource-limited devices | Not as widely adopted as other protocols |
| AWS Greengrass | Comprehensive platform, strong security, cloud integration | Can be complex to set up and manage |
| Azure IoT Edge | Cloud-based, scalable, supports diverse workloads | Requires strong cloud connectivity, potential for vendor lock-in |
Benefits of Edge Computing
Edge computing offers a compelling alternative to traditional cloud computing, particularly in scenarios demanding low latency and high responsiveness. Its distributed architecture brings processing power closer to the data source, leading to significant advantages across various applications. This proximity to data sources dramatically reduces transmission times and allows for real-time decision-making, significantly impacting performance and user experience.Edge computing excels in situations requiring immediate reactions, such as autonomous vehicles or real-time video surveillance.
By processing data locally, edge computing minimizes the reliance on remote cloud servers, enhancing security and privacy while improving responsiveness. This decentralized approach also provides greater resilience against network disruptions, crucial in applications with critical performance requirements.
Performance and Responsiveness Enhancements
Edge computing significantly improves performance and responsiveness by localizing data processing. This proximity to the data source eliminates the need for extensive data transfer to remote cloud servers, resulting in reduced latency and faster processing speeds. This, in turn, leads to quicker feedback loops and more responsive applications, particularly in time-sensitive applications.
Reduced Latency and Data Processing Speed
Reduced latency is a key benefit of edge computing. By bringing computation closer to the data source, the time it takes for data to travel to and from a central cloud server is minimized. This translates to faster data processing speeds, crucial for real-time applications like video streaming, industrial automation, and augmented reality. Latency reductions are often measurable, leading to improved user experience and application performance.
For instance, a video game streamed from a cloud server might experience noticeable lag, whereas a game processed at the edge will provide a smoother, more responsive experience.
Enhanced Security and Data Privacy
Edge computing strengthens security and data privacy by reducing the amount of sensitive data transmitted across potentially vulnerable networks. Processing data locally minimizes the risk of unauthorized access and data breaches that could occur during transmission to a central cloud. This localized processing also allows for stricter data governance and control over data access, enhancing compliance with privacy regulations.
Improved User Experience
Edge computing directly translates into a better user experience. Reduced latency and faster processing speeds result in more responsive applications, improving user satisfaction and engagement. This is evident in real-time applications like video conferencing, where a lag-free experience is paramount. Consider a scenario where a user is interacting with an augmented reality application. Edge computing ensures immediate responses to user actions, providing a seamless and immersive experience.
Examples of Edge Computing’s Impact
Edge computing is increasingly crucial in diverse fields. For instance, in the industrial sector, edge devices can monitor machinery in real-time, enabling proactive maintenance and minimizing downtime. This localized analysis prevents costly equipment failures and ensures optimal performance. In the healthcare sector, edge computing can process medical images quickly, enabling faster diagnoses and treatment decisions, ultimately improving patient outcomes.
These are just a few examples of how edge computing is revolutionizing various industries by enhancing user experience, performance, and security.
Challenges in Edge Computing
Edge computing, while promising significant advantages, presents a range of obstacles that need careful consideration for successful implementation. These challenges span from the management of distributed devices to the intricate security concerns in decentralized data handling. Overcoming these hurdles is crucial for realizing the full potential of edge computing.Implementing edge computing solutions often faces challenges in managing the diverse hardware and software environments across various edge locations.
This heterogeneity introduces complexity into deployment, maintenance, and upgrades. Data security and privacy are paramount concerns, especially with the increased volume of sensitive data being processed at the edge. Maintaining consistent performance across diverse edge locations, often with varying network conditions and resource limitations, is another critical hurdle.
Obstacles to Deploying Edge Computing Solutions
Implementing edge computing solutions is fraught with obstacles, ranging from the intricate management of diverse hardware to the challenges of ensuring consistent performance across disparate locations. A crucial challenge lies in the heterogeneity of edge devices, leading to varying hardware and software configurations. This variation can make deploying and managing the solutions complex. Furthermore, the cost of deploying and maintaining a network of edge devices can be substantial, potentially outweighing the initial benefits.
Complexities of Managing Distributed Edge Devices
Managing a network of distributed edge devices presents unique challenges. The sheer number and geographic dispersion of these devices can make centralized management difficult. Ensuring consistent software updates and maintaining device security across all locations is a major concern. Furthermore, troubleshooting issues in a distributed environment requires specialized tools and expertise. The lack of standardized communication protocols and interoperability issues between devices can also hinder seamless operation.
Challenges Associated with Data Security and Privacy in Edge Computing Environments
Data security and privacy are paramount concerns in edge computing. Data is often collected and processed at the edge, raising the risk of unauthorized access or breaches. Protecting sensitive data in transit and at rest requires robust security measures, including encryption and access controls. Maintaining compliance with data privacy regulations, such as GDPR or CCPA, is another critical challenge.
Furthermore, the distributed nature of edge computing necessitates a decentralized security approach, making it more complex to implement and monitor.
Difficulties in Ensuring Consistent Performance Across Various Edge Locations
Maintaining consistent performance across different edge locations is a significant challenge. Variability in network conditions, bandwidth limitations, and fluctuating power supplies can impact the performance of edge devices. This inconsistency can lead to delays in processing data or even failures in critical applications. Moreover, ensuring predictable response times and low latency across all locations is crucial for many applications, such as real-time video streaming or industrial automation.
Comparison of Challenges and Solutions for Edge Computing Deployments
| Challenge | Description | Potential Solutions |
|---|---|---|
| Heterogeneous Edge Devices | Varying hardware and software configurations across edge devices. | Standardized device interfaces, containerization, and cloud-based management tools. |
| Data Security and Privacy | Risk of unauthorized access and breaches in decentralized data handling. | Robust encryption, access controls, and compliance with data privacy regulations. |
| Distributed Device Management | Complexity in managing numerous geographically dispersed devices. | Centralized management platforms, remote monitoring tools, and automated update systems. |
| Performance Consistency | Variability in network conditions and resource limitations across edge locations. | Network optimization techniques, load balancing strategies, and geographically dispersed caching. |
| Cost of Deployment and Maintenance | High initial and ongoing costs for deploying and maintaining edge infrastructure. | Cloud-based edge computing solutions, shared infrastructure, and optimized hardware choices. |
Edge Computing Use Cases
Edge computing is revolutionizing numerous industries by bringing processing power closer to the data source. This localized processing significantly reduces latency, improves responsiveness, and enhances data security, leading to more efficient and intelligent applications. Its adaptability to diverse environments and requirements makes it a powerful tool for innovation across sectors.Edge computing’s proximity to data sources enables real-time analysis and decision-making, transforming traditional approaches in various fields.
This immediacy is crucial for applications demanding rapid responses and low latency, such as industrial automation, autonomous vehicles, and smart city management. Moreover, it fosters data privacy and security by minimizing the need to transmit sensitive information over vast networks.
Industrial Automation
Edge computing is transforming industrial automation by enabling real-time data processing and control. By processing data locally, edge devices can react to changes quickly and reliably, without relying on a central server. This immediacy reduces delays and improves overall efficiency. For example, in manufacturing plants, edge devices can monitor equipment performance, detect anomalies, and trigger preventative maintenance actions, thereby minimizing downtime and maximizing productivity.
Furthermore, edge computing allows for the development of more sophisticated and complex control systems, enabling more agile and responsive manufacturing processes.
Smart Cities
Edge computing is instrumental in building smarter cities by enabling the collection, processing, and analysis of vast amounts of data from various sources, including sensors and cameras. Edge devices can analyze this data in real-time, enabling proactive responses to challenges like traffic congestion, energy consumption, and public safety concerns. For example, traffic management systems can adjust traffic signals based on real-time data, optimizing traffic flow and reducing congestion.
Similarly, smart lighting systems can automatically adjust brightness levels based on ambient conditions and occupancy, reducing energy consumption.
Healthcare Applications
Edge computing significantly improves healthcare applications by facilitating real-time analysis and processing of patient data, including vital signs, medical images, and sensor readings. This enables rapid responses to critical situations and more informed decision-making. For example, remote patient monitoring systems can collect and analyze patient data in real-time, allowing healthcare providers to identify potential issues and intervene promptly. Edge devices can also process medical images locally, enabling faster diagnoses and treatment plans.
This capability is particularly important in remote areas with limited internet connectivity.
Autonomous Vehicles
Edge computing is essential for autonomous vehicles because it allows for the processing of massive amounts of data from sensors in real-time, without relying on a central server. This localized processing ensures that autonomous vehicles can make rapid decisions in dynamic situations, improving safety and efficiency. For example, edge devices can analyze sensor data from cameras, radar, and lidar to detect obstacles and adjust the vehicle’s trajectory instantaneously.
This capability enables autonomous vehicles to operate safely and reliably in diverse environments.
Financial Services
Edge computing is increasingly being adopted in financial services for tasks like fraud detection and risk management. By processing data locally, financial institutions can detect fraudulent transactions and manage risks more efficiently. This approach significantly reduces the time required to process transactions, enhancing the speed and reliability of financial services. Furthermore, edge computing can improve the security of financial transactions by minimizing the risk of data breaches.
For example, real-time fraud detection systems can flag suspicious transactions quickly, minimizing financial losses.
Security Considerations in Edge Computing
Edge computing, while offering numerous advantages, introduces unique security challenges. Data transmission across various devices and networks, coupled with the decentralized nature of edge deployments, necessitates robust security measures to safeguard sensitive information. The distributed architecture necessitates a comprehensive security strategy to protect data from unauthorized access, modification, or destruction.Edge computing systems are often deployed in remote locations, which can lead to a lack of centralized monitoring and management.
This distributed nature presents vulnerabilities that must be proactively addressed to ensure the integrity and confidentiality of data. Securing edge devices, data transmission channels, and access controls is paramount for preventing malicious actors from compromising the system.
Security Vulnerabilities Specific to Edge Computing
Edge devices, often resource-constrained and deployed in diverse environments, are particularly susceptible to various security vulnerabilities. These include vulnerabilities in firmware, operating systems, and network protocols. The heterogeneity of edge devices can complicate security patching and updates, creating a significant security risk.
Methods for Securing Data Transmission in Edge Environments
Robust encryption protocols, such as TLS/SSL, are crucial for securing data transmission between edge devices and the cloud or other interconnected systems. Data integrity verification mechanisms, including digital signatures, can help detect any unauthorized modifications during transit. Secure communication channels should be established to prevent eavesdropping and tampering. Employing VPNs or other secure networking solutions is also a crucial component.
Importance of Secure Device Management in Edge Computing
Secure device management is critical for maintaining the integrity and security of edge computing systems. This involves secure onboarding procedures, regular software updates, and the ability to remotely manage and monitor devices. Robust access control mechanisms are necessary to limit unauthorized access and ensure that only authorized personnel can interact with the devices. Implementing intrusion detection and prevention systems can proactively identify and mitigate security threats.
Implementing Access Controls for Edge Devices
Access controls should be implemented at multiple levels, from the physical device to the network level and application level. Using strong passwords, multi-factor authentication, and role-based access control can limit unauthorized access to sensitive data. Implementing strict access control lists and policies, tailored to the specific device and its functionalities, is essential for granular control. Regular audits and reviews of access controls are vital to ensure their effectiveness and identify potential weaknesses.
Examples of Edge Computing Security Breaches and Their Impacts
A breach at a smart city traffic management system could disrupt traffic flow and potentially endanger public safety. Compromising industrial automation systems at a manufacturing facility could lead to production downtime, safety hazards, and financial losses. In a healthcare setting, a breach of a remote patient monitoring system could compromise sensitive patient data and potentially affect treatment plans.
These examples highlight the severe consequences of inadequate security measures in edge computing deployments.
Deployment Models for Edge Computing
Edge computing deployment models define how edge resources are organized and managed. These models significantly impact the performance, security, and cost-effectiveness of edge deployments. Understanding different approaches is crucial for selecting the optimal model for specific use cases.Deployment models range from simple, localized setups to complex, distributed architectures. Each model offers unique advantages and disadvantages, and the ideal choice depends heavily on factors such as data volume, latency requirements, security needs, and budget constraints.
This section details various edge deployment models, their pros and cons, and their application in different use cases.
Different Edge Computing Deployment Models
Various deployment models cater to diverse edge computing needs. A well-chosen model can enhance efficiency and optimize resources.
- Centralized Edge Deployment: This model focuses on a central edge data center or hub. Data from various edge devices flows to this central point for processing and storage. This approach is suitable for applications requiring consistent data aggregation and analysis, such as manufacturing operations or financial transactions. Centralized deployment often simplifies management and maintenance. However, it may introduce significant latency, especially for applications with stringent real-time requirements.
- Decentralized Edge Deployment: In contrast to centralized models, decentralized edge deployments distribute processing and storage capabilities across multiple edge nodes. This ensures faster data processing closer to the source, reducing latency. This approach is well-suited for applications demanding low latency and high availability, such as autonomous vehicles or industrial automation. However, it often necessitates a more complex management system to ensure interoperability and data consistency among the distributed nodes.
- Hybrid Edge Deployment: This model combines elements of both centralized and decentralized models. Some data processing occurs at the edge, while more complex tasks or data aggregation are handled centrally. This provides a balance between speed and control, which is ideal for use cases demanding both low latency and centralized data analysis. A hybrid approach is beneficial for scenarios requiring a combination of real-time processing and comprehensive data analysis.
- Cloud-Based Edge Deployment: This model leverages cloud infrastructure to support edge computing capabilities. Edge devices connect to cloud-based resources for data processing, storage, and application execution. This model offers high scalability and flexibility, making it ideal for rapidly evolving applications and growing data volumes. However, it often depends on reliable network connectivity, and security concerns associated with data transmission to the cloud need careful consideration.
Centralized vs. Decentralized Edge Architectures
The choice between centralized and decentralized edge architectures depends on the specific needs of the application.
- Centralized Edge Architecture: This architecture offers centralized control and management, making it easier to maintain and manage a consistent data processing pipeline. It is suitable for scenarios requiring data aggregation and analysis, but can introduce higher latency for real-time applications. Data consistency is typically maintained, though this comes at a potential cost of complexity.
- Decentralized Edge Architecture: This architecture distributes data processing and storage across multiple edge nodes, reducing latency and enhancing fault tolerance. However, managing and ensuring data consistency across multiple nodes becomes more complex. Decentralized architectures are better suited for applications requiring high availability and real-time data processing, like autonomous vehicles.
Deployment Strategies for Specific Use Cases
Different deployment strategies are appropriate for different use cases.
- Industrial Automation: A hybrid model combining localized processing with a central data hub is suitable for industrial automation, as it allows for real-time control while also providing opportunities for large-scale data analysis. The central hub can process and analyze data for improved decision-making, while localized processing ensures quick responses to events.
- Autonomous Vehicles: A decentralized model, distributing processing across multiple vehicles, is crucial for autonomous vehicles to enable real-time decision-making and responsiveness to changing road conditions. The distributed processing mitigates latency and ensures high availability.
Comparison of Deployment Models
| Deployment Model | Scalability | Security | Costs |
|---|---|---|---|
| Centralized | Good, but limited by central point | Potentially higher risk at central point | Moderate, potentially lower for initial setup |
| Decentralized | High, scalable across multiple nodes | Higher security complexity due to multiple points | High, as it involves multiple nodes and communication |
| Hybrid | Good, balancing centralization and decentralization | Balance of centralized and decentralized security concerns | Moderate, balancing cost of both approaches |
| Cloud-Based | High, scalable cloud resources | Relies on cloud security, requiring careful consideration | Variable, depending on cloud usage |
Edge Computing and AI
Edge computing and artificial intelligence (AI) are increasingly intertwined, creating powerful synergies for various applications. The ability to process data locally at the edge, combined with AI algorithms, enables real-time insights and actions, leading to faster responses and improved decision-making. This synergy is particularly valuable in scenarios requiring immediate reactions, such as autonomous vehicles or industrial automation.The deployment of AI algorithms on edge devices allows for localized processing, minimizing latency and bandwidth requirements.
This is crucial for tasks demanding rapid responses, like object detection in surveillance systems or predictive maintenance in industrial settings. The benefits of running AI models at the edge extend beyond speed; they also enhance privacy and security by keeping sensitive data close to its source.
Relationship Between Edge Computing and AI
Edge computing provides the platform for AI algorithms to operate effectively. By bringing the processing power closer to the data source, edge computing reduces latency and reliance on centralized servers, allowing AI models to respond quickly to real-time events. This proximity is critical for AI applications requiring rapid decision-making, like autonomous driving or real-time fraud detection.
Deployment of AI Algorithms on Edge Devices
AI algorithms are deployed on edge devices through various methods, including pre-trained models, which are optimized for specific tasks, and custom-trained models. Pre-trained models, downloaded and optimized for edge devices, enable rapid deployment and require less processing power. Custom-trained models, tailored to a specific edge environment, can offer superior accuracy but require more computation resources and time.
Benefits of Running AI Models at the Edge
Running AI models at the edge offers several advantages. Firstly, it significantly reduces latency, enabling faster responses and quicker decision-making. Secondly, edge AI minimizes the reliance on centralized servers, reducing bandwidth consumption and network congestion. Thirdly, processing data locally improves privacy and security, as sensitive data remains within a controlled environment.
Improving Real-time Decision-Making with Edge AI
Edge AI significantly enhances real-time decision-making by reducing latency and enabling immediate responses. Consider a smart factory; edge AI can analyze sensor data in real-time to identify potential equipment failures, allowing for preventative maintenance and minimizing downtime. Similarly, in autonomous vehicles, edge AI processes sensor inputs, enabling quick reactions to unexpected situations.
Processing Power for Different AI Tasks
The processing power required for AI tasks on edge devices varies considerably. Simple tasks, such as image classification for basic object detection, demand less processing power compared to more complex tasks, like natural language processing or sophisticated object tracking. This difference in processing needs necessitates careful consideration of the specific AI task and the available resources of the edge device.
A table showcasing this difference is presented below:
| AI Task | Processing Power Requirement (Approximate) | Edge Device Suitability |
|---|---|---|
| Simple Object Detection (e.g., identifying a stop sign) | Low | Microcontrollers, small embedded systems |
| Complex Object Tracking (e.g., tracking multiple objects in a crowded scene) | Medium | Edge gateways, specialized AI processors |
| Natural Language Processing (e.g., analyzing customer feedback) | High | High-performance edge servers, specialized AI chips |
Future Trends in Edge Computing
Edge computing is rapidly evolving, driven by the need for faster, more reliable, and localized data processing. This dynamic landscape is marked by emerging technologies and a significant impact from advancements in networking, especially 5G. The future of edge computing promises a more distributed and intelligent approach to data management, leading to new possibilities in various sectors.
Emerging Trends and Technologies
The edge computing landscape is characterized by a diverse range of technologies continuously developing and integrating. This includes advancements in hardware, software, and networking capabilities. The convergence of AI, machine learning, and IoT devices further fuels innovation in edge computing, enabling sophisticated real-time data analysis and decision-making. Real-time processing and data analysis at the edge are crucial for applications requiring immediate responses, such as autonomous vehicles or industrial automation.
Impact of 5G and Other Networking Advancements
G, with its ultra-low latency and high bandwidth, is transforming edge computing. This allows for more efficient data transfer and processing closer to the source, reducing the time lag between data collection and response. Further advancements in networking technologies, including improved connectivity and reliability, are expected to expand the potential of edge computing across diverse environments. Other networking advancements like Wi-Fi 6E and satellite internet technologies are contributing to the broader reach and applicability of edge computing.
Potential Future Applications of Edge Computing
Edge computing is poised to revolutionize several industries. Potential future applications include enhanced remote healthcare monitoring, enabling real-time diagnostics and treatment recommendations. Smart cities can benefit from real-time traffic management and environmental monitoring, leading to more efficient urban planning. Furthermore, edge computing can optimize industrial automation by providing immediate responses to production processes, improving overall efficiency.
Innovative Edge Computing Solutions in the Pipeline
Several innovative edge computing solutions are currently under development. One example is the development of edge AI platforms, designed to enable real-time decision-making in various contexts. These platforms are tailored to specific industries, optimizing the use of AI at the edge. Furthermore, the emergence of specialized hardware optimized for edge computing tasks will significantly improve performance and efficiency.
Projections on the Growth of Edge Computing
The growth of edge computing is projected to be substantial in the coming years. Market research indicates a significant increase in the adoption of edge computing solutions, driven by the need for low-latency applications and real-time data processing. The expanding use of IoT devices and the growing importance of data-driven decision-making will contribute to this growth. For instance, the rise of autonomous vehicles relies heavily on edge computing for real-time processing and decision-making, demonstrating a crucial application of edge technology.
Case Studies
Edge computing is rapidly transforming various industries, and understanding its successful implementations is crucial for appreciating its potential. Case studies offer valuable insights into the real-world applications, benefits, and challenges of edge computing deployments. These studies provide concrete examples that illustrate how organizations are leveraging edge technology to improve efficiency, reduce latency, and enhance decision-making.A multitude of factors influence the success or failure of edge computing projects, including the specific industry, the chosen deployment model, and the technical capabilities of the edge devices.
Analyzing these case studies allows for a deeper understanding of the complexities and nuances involved in deploying and managing edge solutions.
Edge Computing in Manufacturing
The manufacturing sector is increasingly adopting edge computing to enhance real-time monitoring, predictive maintenance, and automation. Edge devices deployed on factory floors collect data from machines, sensors, and processes. This data is processed locally, enabling faster responses to anomalies and preventing costly downtime. This localized processing minimizes latency, allowing for quicker decision-making and improved operational efficiency.
- A leading automotive manufacturer implemented edge computing to monitor the health of its assembly line robots. By processing sensor data locally, the manufacturer identified and resolved potential mechanical failures before they caused significant disruptions, resulting in a 20% reduction in downtime and a 15% improvement in production output.
- A large appliance manufacturer uses edge computing to optimize energy consumption in its factories. By analyzing data from smart sensors on production lines, the company identified inefficiencies and adjusted processes to minimize energy waste. This resulted in a 10% decrease in energy consumption and a corresponding reduction in operational costs.
Successful Edge Computing Implementation in Retail
Retail applications leverage edge computing to personalize customer experiences and optimize store operations. Real-time data analysis at the edge empowers retailers to respond swiftly to changing customer preferences and optimize inventory management.
- A major retail chain implemented edge computing to personalize in-store recommendations for customers. By analyzing real-time data on customer preferences and product placement, the company tailored recommendations, increasing sales by 12%.
- Another retail chain used edge computing to improve inventory management. By analyzing data on product demand and sales patterns at individual stores, the company optimized stock levels, reducing waste and improving profitability.
Challenges and Solutions in Healthcare Edge Deployments
Edge computing in healthcare offers the potential for real-time analysis of patient data, improved diagnostic capabilities, and remote patient monitoring. However, security concerns and the need for reliable network connectivity remain significant challenges.
- One challenge is the secure transmission and storage of sensitive patient data. Implementing robust security protocols and encryption mechanisms is crucial. A solution involves using secure communication channels and employing strong authentication methods to protect the integrity of data.
- Reliable connectivity is another significant challenge, particularly in remote or rural areas. A potential solution includes using multiple communication channels, employing cellular backhaul, or leveraging satellite technology to maintain connectivity in diverse settings.
Summary of Case Studies
| Industry | Specific Use Case | Key Benefits | Challenges | Solutions |
|---|---|---|---|---|
| Manufacturing | Predictive maintenance of assembly line robots | Reduced downtime, improved production output | Data security, connectivity | Secure communication channels, robust authentication |
| Retail | Personalized in-store recommendations | Increased sales, improved customer experience | Data privacy, real-time processing | Data anonymization, robust edge infrastructure |
| Healthcare | Remote patient monitoring | Improved patient care, enhanced diagnostics | Data security, connectivity in remote areas | Secure communication channels, multiple backhaul options |
Conclusion
In conclusion, edge computing presents a powerful paradigm shift in data management and processing. Its ability to improve performance, security, and user experience across diverse applications makes it a crucial technology for the future. While challenges remain, the potential benefits and innovative use cases are substantial, making edge computing a field ripe with opportunity.
Questions Often Asked
What is the difference between edge computing and cloud computing?
Edge computing processes data closer to its source, reducing latency and improving responsiveness. Cloud computing, on the other hand, centralizes data processing in a remote data center.
What are some common use cases for edge computing?
Edge computing is used in various industries, including industrial automation, smart cities, healthcare, and autonomous vehicles, enabling real-time data processing and decision-making.
What are the security concerns of edge computing?
Security is a crucial aspect of edge computing. Securing data transmission, managing edge devices, and implementing robust access controls are paramount to mitigate risks.
What role does AI play in edge computing?
AI algorithms are increasingly deployed on edge devices, enabling real-time decision-making and enhancing the capabilities of edge computing systems.





